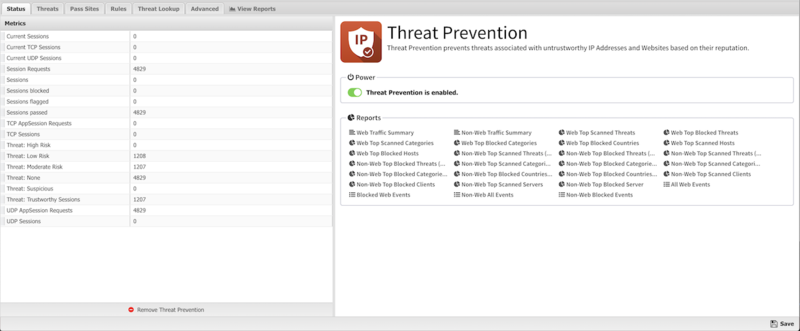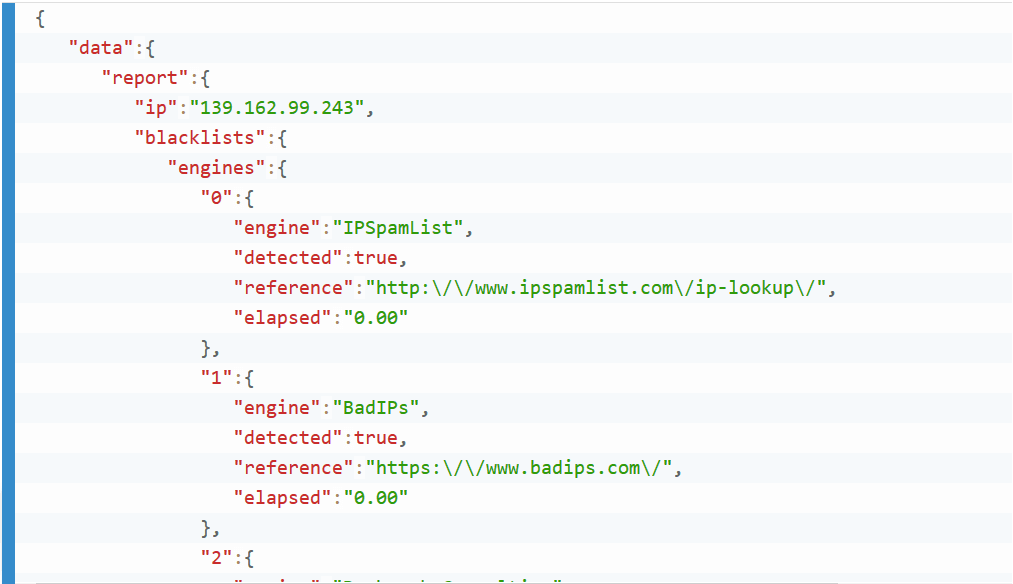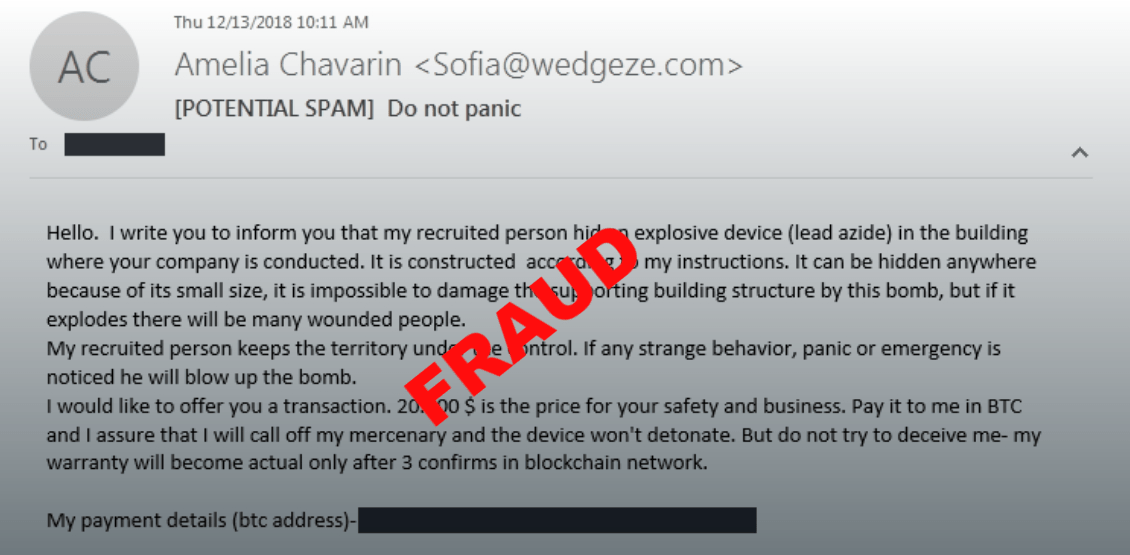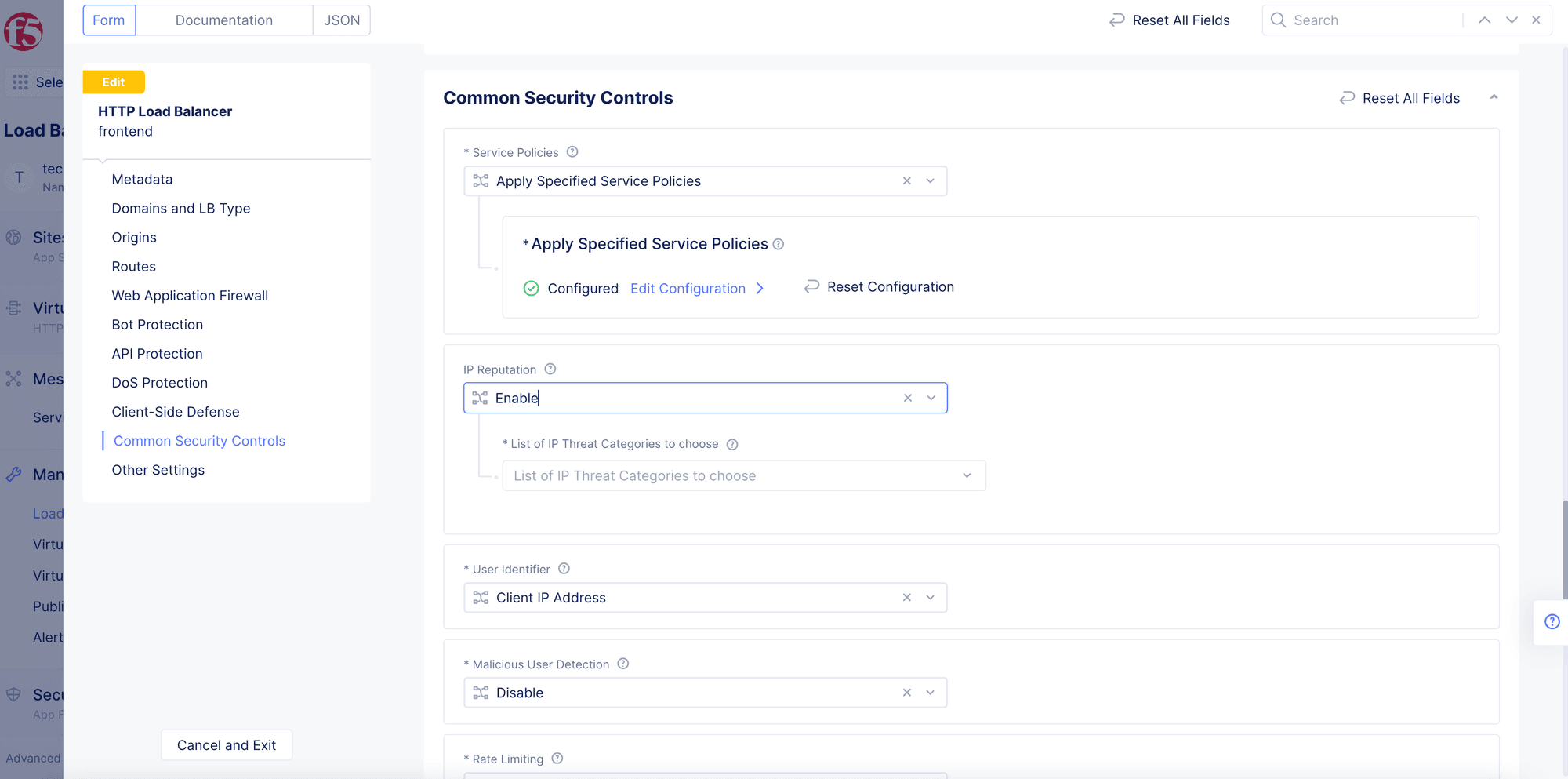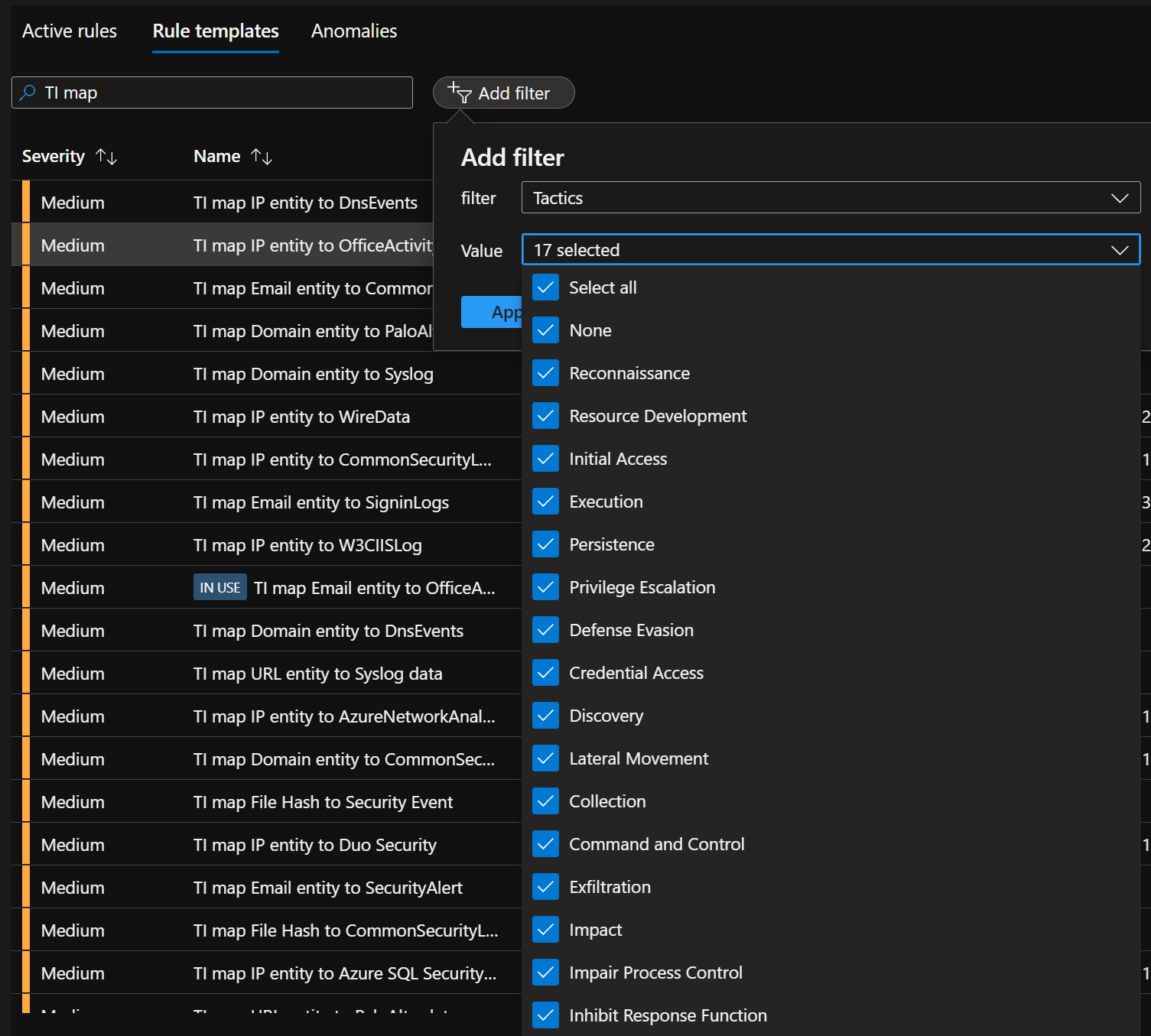
Microsoft Sentinel Threat Intelligence – Part III – Using your TI data with Analytics Rules - Cyber Geeks | Cyber Security & Cloud Computing

Threat Actors Have Grown Smarter in Their DNS Attacks. Here's How Companies Should Respond... - EfficientIP

Intellectual Property Theft: A Threat to Working People and the Economy — Department for Professional Employees, AFL-CIO
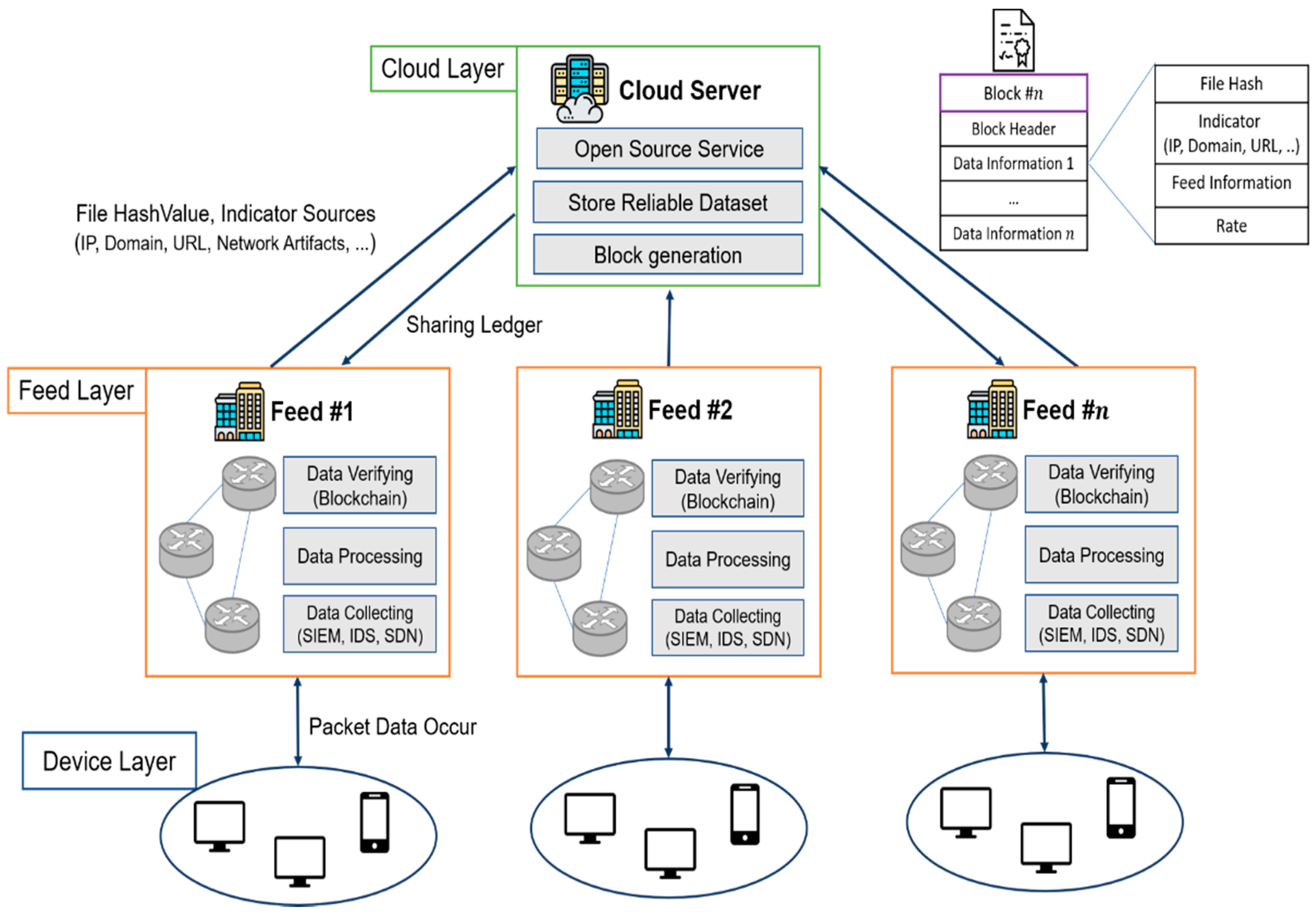
Sustainability | Free Full-Text | Blockchain-Based Cyber Threat Intelligence System Architecture for Sustainable Computing